Great Place To Work® Institute, Inc. External Security Policy
1. General Business Information.
This Policy is intended to help communicate externally to Companies the Security Policy used by GPTW as well as the Network Affiliates and Partners of GPTW and is incorporated by reference into their respective Agreements
1. General Business Information.
GPTW provides products and services assessing workplace culture, performance, certification, and accreditation to assist companies and organizations in evaluating and improving their workplaces. GPTW was incorporated in the State of California on June 30, 1998 and is a privately-held company. It is headquartered in Oakland CA at 1999 Harrison Street, Suite 2070.
The FEIN for GPTW is 91-1917672 and its DUNS number is 05 1812683. There have been no material claims or judgments against GPTW in the last 5 years and GPTW has never suffered a data loss or security breach.
2. Policy to Safeguard Company Data.
Data security is of paramount importance to GPTW. GPTW has robust policies in place to manage and secure Company data.
The GPTW survey software platform (“Emprising”) is a SaaS application hosted in the Microsoft Azure Cloud. The Emprising application and associated data is hosted in a series of virtual networks which are wholly separate from our general corporate network infrastructure. Our public website (www.greatplacetowork.com) is hosted in the Amazon AWS cloud.
Human Resource Security.
GPTW’s Human Resources takes several steps to help protect Company data. GPTW performs background verification checks on all candidates for employment and our employees must sign the terms and conditions of employment. Furthermore, GPTW conducts mandatory semi-annual privacy and security awareness training for all staff. GPTW will notify Company if a GPTW employee who had access to Company data has been terminated or changed roles within GPTW that warrants an “Appropriateness of access review.”
Data Collection.
GPTW only collects data needed for its intended purposes like Great Workplace Certification, Best Workplaces Lists, Advisory and High Trust Culture Consulting engagements, Accelerated Leadership Performance, etc.
Data Access.
Access to Company data is only granted to those with a legitimate need. Company data is only accessed by GPTW employees that are authorized based on job role. Survey access is controlled so that survey respondents cannot see another’s responses. Data is partitioned and separated so that Company users cannot see another company’s data.
Access Control.
GPTW has a documented onboarding and offboarding policy which includes a formal user registration and de-registration process to enable assignment of access rights, unique IDs for all users, a periodic review of access rights with owners of the information systems or services, restrictions and control of privileged access rights by management, an authorization process to allocate and control privileged access rights, monthly review of privileged access, password requirements (such as minimum length, complexity, periodicity to change, password history), and encrypted passwords in store and transmit. GPTW will notify Company within 72 hours from GPTW becoming aware of any confirmed or suspected leak of Company data. Enforcement mechanisms are applied to GPTW employees who violate privacy policies or confidentiality requirements. Separate virtual local area networks (VLANs) are created for BYOD systems or other untrusted devices. Regular scanning is performed for unauthorized software and alerts are generated when it is discovered on a system.
GPTW and Network Hardware.
On premises servers are in a locked, climate-controlled server room with access limited to authorized personnel. Company data is encrypted in transit and in storage using a commercially available dual key AES 256 bit encryption software. Systems with active removable media devices are configured so that they conduct an automated anti-malware scan of removable media when it is inserted. All email attachments entering GPTW’s email gateway are scanned, and email is blocked if it contains malicious code or file types commonly known to be associated with malicious software. This scanning is done before the email is placed in the user’s inbox and includes filtering of the email content as well as embedded links within the email content. GPTW has never experienced a security incident (such as a data breach, loss of customer data, or network intrusion). Hard disks or storage memory of all laptops are encrypted. GPTW supports e-mail encryption (SMTP/TLS, or a similar mechanism). A process is established and followed to revoke user access upon termination of employment or contractual relationship. In addition to an inventory of hardware, there is an inventory of information assets that identifies the related hardware assets (e.g., servers) where the asset is located.
GPTW Network Monitoring.
Administrative privileges are limited to users who have both the knowledge necessary and a business need to perform administrative activities. System-specific configuration management tools are deployed (such as Active Directory Group Policy for Microsoft Windows environments) that automatically enforce and redeploy configuration settings to systems at regularly scheduled intervals. Automated tools are deployed to continuously monitor workstations and servers for active, up-to-date anti-malware protection. This protection includes appropriate use of anti-virus, anti-spyware, and personal firewalls. Malware detection events are sent to enterprise anti-malware administration tools and event log servers. Our internally developed web applications are tested for common security weaknesses using automated remote web application scanners prior to deployment, whenever updates are made to the application, and on a regular recurring basis. Testing includes behavior under denial of service or resource exhaustion attacks. SPF and DKIM are implemented by deploying appropriate records in DNS and enabling receiver-side verification in mail servers to prevent email spam by detecting email spoofing.
GPTW Wireless Network.
Each wireless device connected to the trusted employee network matches an authorized configuration and security profile. All wireless traffic leverages at least Wi-Fi Protected Access 2 (WPA2) protection. Wireless networks use authentication protocols such as Extensible Authentication Protocol-Transport Layer Security (EAP/TLS). Personally-owned devices, connect to a wireless network that is logically separate from the enterprise network. All registered devices must be scanned and follow corporate policies for host hardening and configuration management.
GPTW Backup Media.
Data on backup media is tested on a regular basis by performing a data restoration process to ensure that the backup procedure is working properly. Key personnel are trained on both backup and restoration processes. Alternate personnel are also trained in case primary personnel are not available. Backups are properly protected via physical security or encryption when they are stored, as well as when they are transmitted across the network. This includes network-based backups and use of cloud-based services. End-of-life backup media is securely erased/destroyed.
GPTW Network Devices.
Network devices (e.g., firewalls, routers, switches, etc.) are built using standard secure configurations defined for each type of network device in use in GPTW. The standard secure configurations are documented, approved, and regularly reviewed. Any deviations from the standard configuration or updates to the standard configuration are documented and approved by authorized personnel. At network interconnection points (e.g., Internet gateways, third party network connections, internal network segments with different security controls etc.), ingress and egress filtering are implemented to allow only those ports and protocols with an explicit and documented business need. All other ports and protocols are blocked. Network devices are managed using encrypted sessions.
GPTW Network Firewalls.
Host-based firewalls are applied on endpoint systems and include a default-deny rule that drops all traffic except those services and ports that are explicitly allowed. Unless required to be visible to the Internet or an untrusted network for business purposes, all systems are placed on an internal VLAN and given a private address. Network services required for business use on the internal network are reviewed on a regular basis to reconfirm the business need. Services that are enabled for projects or limited engagements are disabled when they are no longer required and properly documented. Critical services (e.g., DNS, DHCP) operate on separate physical or logical host machines. Application firewalls block unauthorized traffic.
GPTW Password Policy.
Default passwords (including those for applications, databases, operating systems, routers, firewalls, wireless access points, and other infrastructure) are changed prior to deployment. Administrative accounts are used only for system administration activities, and not for general business activities such as reading email, composing documents, or Internet access. Passwords cannot be reused for a defined period of time, consistent with the GPTW’s password policy. Systems log any changes related to access control (e.g., adding or removing user accounts or privileges associated with a user). All system accounts are periodically reviewed. Any account that cannot be associated with a business process and owner is disabled. All user accounts have an expiration date associated with the account. All users are automatically logged off after a standard period of inactivity. User accounts are locked out for a defined period of time following a defined number of unsuccessful logon attempts. Multi-factor authentication is used for all named employee accounts.
GPTW Network Traffic Control.
Network perimeters are designed and implemented so that all outgoing traffic to the Internet must pass through at least one firewall or proxy. All devices remotely logging into the internal network are managed by the enterprise, which includes remote control of the device configuration, installed software, and patch levels. An internal network segmentation scheme has been implemented to limit traffic to only those services needed for business use across GPTW’s internal network. Synchronized time sources are used (e.g., Network Time Protocol: NTP) from which all servers and network equipment retrieve authoritative time information on a regular basis to ensure that timestamps in logs are consistent. Network boundary devices (including firewalls, inbound and outbound proxies) are configured to log traffic. GPTW has established and follows procedures for secure data destruction. GPTW has established a written incident response plan that includes definition of roles and responsibilities for incident management. Senior management is appropriately represented (with input and decision-making authority) in the incident management process. The incident response plan includes procedures for the analysis of events and the criteria for determining if the event should be escalated to an incident. Procedures include roles and responsibilities for personnel and requirements for internal (e.g., Compliance, Communications, Legal, Executive Team) and external (e.g., Law Enforcement, Customer) notifications. GPTW publicly maintains contact information on its website that enables third party members of the public to report an information security incident. Procedures have been developed and disseminated to GPTW personnel related to the mechanisms for identifying and reporting an information security incident. This information is included as part of routine security awareness training.
GPTW Network Periodic Testing.
The network is designed using appropriate use of network segmentation. The enterprise network is segmented into multiple, separate trust zones to provide more granular control of system access and additional network boundary defenses. Vulnerabilities identified as high severity or high risk are remediated in an expedited manner following their identification. Periodic external and internal penetration tests are conducted to identify vulnerabilities and attack vectors that can be used to exploit GPTW’s systems. Findings identified in vulnerability assessments are documented, prioritized and remediated. Social engineering is included within penetration tests. Critical vulnerabilities are patched in an expeditious manner consistent with an established patch management process.
GPTW Change Management Process.
A change management process and procedure is implemented to manage and control changes to production applications and infrastructure. Management approves all changes prior to implementation. Application changes are tested by staff other than developers prior to implementation. Standard secure operating system configurations are established and used. Patch management processes are implemented that ensure security patches are installed within a timely manner following their release. Patching processes encompass the entirety of the IT operating environment including applications, databases, operating systems, utilities and network infrastructure. All remote administration activities are performed over secure channels that incorporate use of appropriate levels of encryption and multi-factor authentication. An established process and associated configuration management infrastructure is deployed for configuration control of laptops. The process includes secure remote wiping of lost or stolen devices. Anti-malware software and signature auto-update features allow administrators to manually deploy updates to all machines when required. Separate environments are maintained for production and non-production systems. All systems that store logs have adequate storage space for the logs generated on a regular basis (so that log files will not fill up between log rotation intervals). Devices are configured to log access control events associated with a user attempting to access a resource (e.g., a file or directory) without the appropriate permissions. Failed logon attempts are also logged. GPTW uses a secure wipe (multi-pass overwrite) solution to securely delete SLM NPI, PII or proprietary data on hard drives or other media when data retention is no longer required.
Software.
In-house-developed and third-party-procured web and other application software is tested for coding errors and vulnerabilities, prior to deployment. In particular, input validation and output encoding routines of application software are carefully reviewed and tested. All source code is centrally managed and retained in a source code repository. A software inventory tool is deployed throughout the operating environment that covers various devices in use, including servers, workstations, and laptops. The software inventory tool records relevant information such as software version number and patch level.
Policy Reviews.
Data privacy & security policies are reviewed monthly.
3. Policy to Safeguard Company Employee Data
Data Collection.
The GPTW Emprising™ survey and analytics software platform operates by uploading to Emprising an Employee Data File (EDF) containing an email address list for the Company’s Employees taking the survey and, optionally, other information such as pre-coded demographics etc. of the Company’s Employees. The EDF can be uploaded to Emprising either by GPTW or directly by the Company. When the Company Survey starts running, the email list from the EDF is used to generate a Personalized Invite to each Company Employee which is a log-in identifier unique to each Company Employee. When the Company Survey closes, the link is broken between the EDF and the Company Employee Data containing the Survey Responses of the Company Employees which disassociates and physically separates the EDF from the Company Employee Data. After the survey closes, the Company Employee Data does not contain the name or email address of the Company Employee. Within five business days after closing the Company Survey, the functionality of the survey is confirmed by GPTW and the EDF is deidentified.
The types and categories of Company Personal Data to be processed are found in the demographic section and Trust Index questions of the survey. If the Company chooses to include demographic data in the survey responses, that demographic data is made part of the EDF which then populates the Survey Responses when the Company Employee uses their unique log-in identifier to take their survey. After the Company Survey closes, any demographic data remains a part of both the EDF and the Company Employee Data. To protect the confidentiality of the Company Employee Data, GPTW uses a suppression algorithm. GPTW will not report on Assessment results in which fewer than five (5) people in a Company demographic group have responded. The Personalized Invite explains that the results of this survey will be used to determine if the Company can be Great Place To Work-Certified, qualify to be on one of the GPTW Best Workplaces lists and to potentially publish an unbiased review of your workplace on our Great Place To Work Reviews website. The Company Employee is assured that their participation is completely confidential and voluntary. The Survey Responses come directly to GPTW. Besides responding to statements, there are two open-ended questions soliciting an essay style response. The Company has the option to add additional open-ended questions. The Company Employee is advised that should they choose to use their name or the names of others in the essay style responses to the open-ended questions, they will appear verbatim and the Company may read them. Comments you supply may also be quoted in GPTW articles or reviews, but they will never be associated with your name or other personally identifying information.
The nature and purpose as well as the subject matter and duration of the Processing of the Company Personal Data is to collect Company employee survey data for processing and archiving scientific and historical research purposes and statistical purposes assessing workplace culture, performance, and accreditation to assist organizations in evaluating and improving their workplaces. This exact language is found in Article 89 of the GDPR.
GPTW uses commercially reasonable efforts consistent with industry standards to collect, transmit, store, protect and maintain the Data and Company Data obtained through the Services. GPTW represents and warrants that during processing or the term of the client’s engagement that it complies with the European Union (EU) 2016 General Data Protection Regulation (GDPR), the California Consumer Privacy Act of 2018 AB 375 (CCPA). This warranty is stated in Section 8 (Data Privacy) of the GPTW Products and Services Agreement which governs the terms of the engagement with GPTW clients and which has the following link on the bottom of the GPTW homepage: https://www.greatplacetowork.com/products-services-agreement
As advised in the GDPR, GPTW maintains a full-time Chief Data Protection Officer (CDPO) and staff to ensure compliance with all Data Protection Laws. The CDPO reports directly to the CEO of GPTW. GPTW also employs full-time Certified Information Privacy Practitioner (CIPP) and staff who is certified under the NIST standard as administered by the International Association of Privacy Professionals at www.iapp.org.
Data Access.
Access to Company data is only granted to those with a legitimate need. Company data is only accessed by GPTW employees that are authorized based on job role. Survey access is controlled so that survey respondents cannot see another’s responses. Data is separated and partitioned so that Company users cannot see another company’s data.
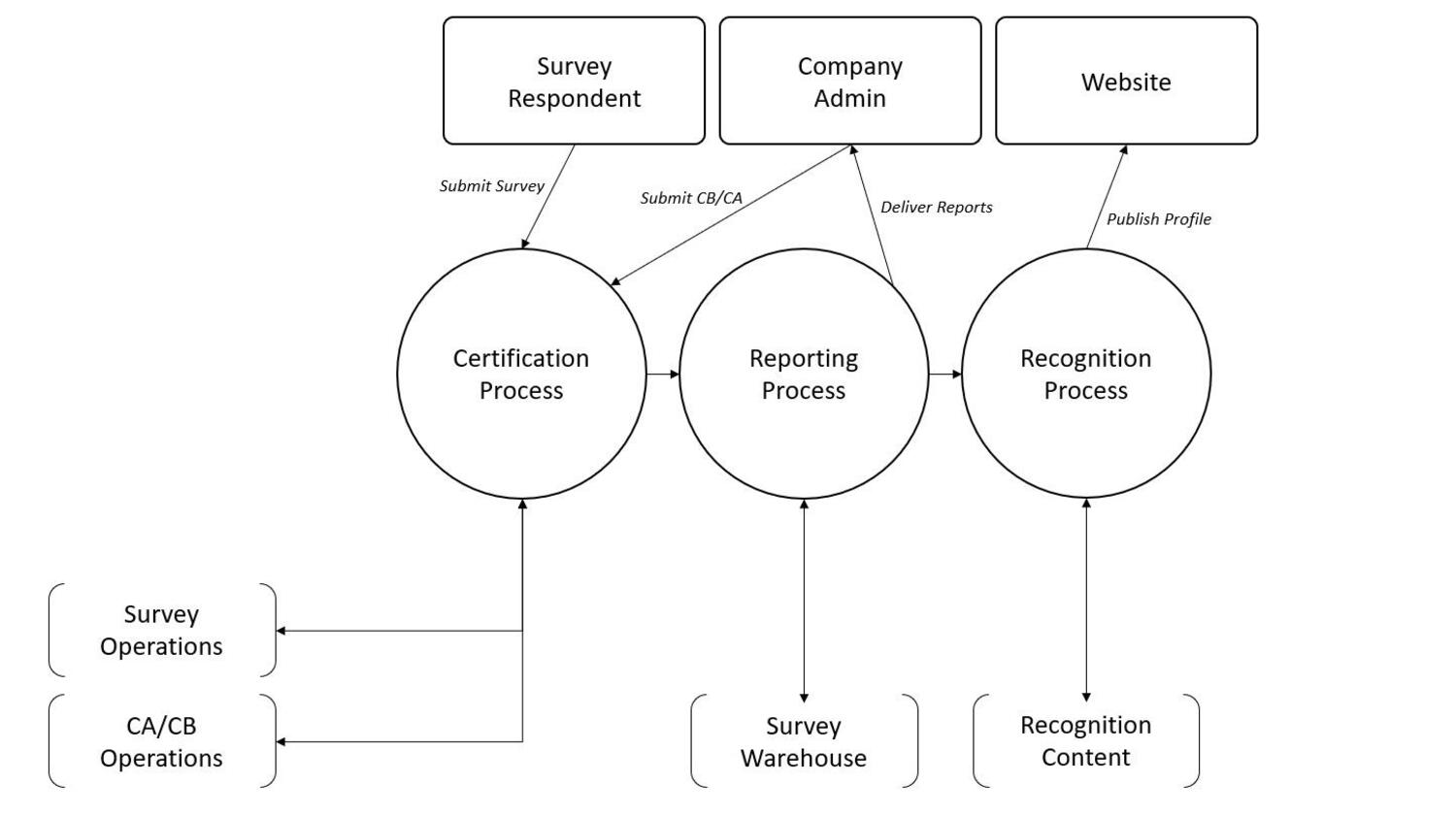
4. Data Flow Diagrams.
Data Flow Diagram For the GPTW Certification Process:
5. Data Privacy.
GPTW maintains a full-time Chief Data Protection Officer (CDPO) and staff to ensure compliance with these policies. The CDPO reports directly to the CEO of GPTW. GPTW also employs full-time a Certified Information Privacy Practitioner (CIPP) who is certified by the International Association of Privacy Professionals at www.iapp.org whose credentials are accredited by the American National Standards Institute (ANSI) under the International Organization for Standardization (ISO) standard 17024:2012. ANSI is an internationally respected accrediting body that assesses and accredits certification programs that meet rigorous standards. ANSI’s personnel certification accreditation program was the first such program in the United States to fulfill the requirements of ISO/IEC 17011, which represents the global benchmark for accreditation body practice.
GPTW complies with the European Union (EU) 2016 General Data Protection Regulation (GDPR), the California Consumer Protection Act of 2018 AB 375 (CCPA), the Asia-Pacific Economic Cooperation (APEC) Cross Border Privacy Rules. GPTW is also certified under the US/EU and US/CH Privacy Shield. This Agreement incorporates all of the clauses recited in the 2010/87 European Commission Decision STANDARD CONTRACTUAL CLAUSES. GPTW collects Data for processing and archiving scientific and historical research purposes and statistical purposes assessing workplace culture, performance, and accreditation to assist organizations in evaluating and improving their workplaces. This exact language is found in Article 89 of the GDPR. The types and categories of Company Personal Data to be processed is found in the demographic section and Trust Index questions of the survey. GPTW DOES NOT SELL PERSONAL DATA to any third party.
In connection with the Services, GPTW may receive, process and store Personal Data in the United States or other jurisdictions. Personal Data received by GPTW will be protected by GPTW as described in the Section above. In the event that consent of any individual is required to be obtained before transfer of Personal Information to GPTW, Company is responsible for obtaining the consent of any affected individual. Said consent needs to be freely given, specific, informed, unambiguous and given by a statement or clear affirmative action.
Scoped Data
GPTW has a data classification and retention program for Scoped Data that identifies the data types that require additional management and governance. GPTW has a documented response program to address privacy incidents, unauthorized disclosure or breach of Scoped Data. Scoped Data is not disclosed to third parties, within or outside the United States. GPTW has a documented privacy program with administrative, technical, and physical safeguards for the protection of Scoped Data including the use of encryption tools.
Compliance and Incident Response
All privacy complaints and privacy incidents are directed and responded to by the Director of Legal Affairs. Enforcement mechanisms are applied to GPTW employees who violate privacy or confidentiality policies.
6. Policy Regarding Ownership and Use of Data.
Company Data
Company Data means Company’s proprietary data and information that Company provides to GPTW so that GPTW may, as part of the Services, conduct an Assessment (e.g., demographic and corporate information necessary to distribute the Survey to participants (such as email address, employee ID, and other personally identifying information) and the data provided by Company to GPTW for the Culture Audit). For the avoidance of doubt, Company Data does not include either Aggregate Data or Raw Data as defined below. The Company Data and all Intellectual Property Rights remain the exclusive property of the Company. GPTW will use Company Data solely to perform the Services and in a manner that is compatible with the purposes for which such Company Data is furnished to GPTW or subsequently authorized to be used, and GPTW will ensure that any Personal Data included in Company Data is properly maintained and protected.
Aggregate Data and Raw Data
Aggregate Data means (a) the Company-specific information, data, and content contained in any report(s) delivered by GPTW to Company pursuant to this Agreement; and (b) any other aggregated data that is derived from the Raw Data and that is delivered by GPTW to Company pursuant to this Agreement. For the avoidance of doubt, Aggregate Data does not include any Raw Data or Company Data. Raw Data means the confidential and anonymous responses received by GPTW from Company and Company’s employees in connection with, among other things, the Trust Index Survey(s) and/or Culture Audit(s), Culture Brief(s), focus groups, and one-to-one interviews administered by GPTW pursuant to this Agreement. For the avoidance of doubt, Raw Data does not include any Aggregate Data or Company Data. The Raw Data and the Aggregate Data obtained through the Services provided, and all Intellectual Property Rights are and will remain the exclusive property of GPTW. The Raw Data will not be provided to the Company by GPTW in order to protect the confidentiality of Company respondents. GPTW intends to use the Aggregate Data solely for the internal purposes of GPTW, including without limitation for benchmarking, creation of best practices and other R&D purposes. GPTW will not share non-anonymous, Company-specific information about the Company’s results with any third parties without first receiving prior written permission from Company (i.e., the Data is not intended to be associated with the Company or any individual Company employee). This will not apply in connection with any of the Best Workplaces Lists. Reports provided by GPTW to Company may be distributed internally by Company, but any external distribution requires prior written approval from GPTW which will not be unreasonably withheld. Aggregate Data and Raw Data are collectively referred to as Data herein.
Intellectual Property
The GPTW Intellectual Property, and all Intellectual Property Rights therein will remain the exclusive property of GPTW or its Affiliate Licensees. The Company is not acquiring any rights to any GPTW Intellectual Property because of the Agreement between both parties. Without GPTW’s prior written approval, which may be withheld in GPTW’s sole discretion, the Company will not use or re-use any GPTW Intellectual Property in any manner other than pursuant to its receipt of the Services during the Term (including in any surveying conducted either in-house or with another vendor outside of the scope of the Agreement).
Confidentiality
All information provided by the Company to GPTW or otherwise obtained by GPTW as a receiving Party relating to the business or operations of the Company or its clients or any person, firm, company or organization associated with the Company, will be treated by GPTW as confidential, and GPTW will not disclose the same to third parties without the prior written consent of the Company. The Parties acknowledge and agree that the confidential information of the Company does not include the Raw Data and the Aggregate Data, which are confidential information of GPTW.
7. Operations Security.
GPTW has the following policies in place regarding Operations Security:
- Detection, prevention and recovery controls to protect against malware.
- A formal policy prohibiting the use of unauthorized software by GPTW employees.
- An established process to define organizations’ requirements for backup of information, software and systems.
8. Communications Security.
GPTW has the following policies in place regarding Communications Security:
- Firewall protection for all systems and Internet connectivity.
- VPN and/or Encryption for sensitive information that would otherwise pass over public networks.
- Two-factor authentication for named employee accounts
9. System Acquisition, Development and Maintenance.
As part of GPTW’s information security requirements, we include the information security requirements for new information systems or enhancement of existing information systems, use formal change control process to all changes to systems within the development life cycle, maintain a version control for all software updates and restrict and control modifications to software packages by limiting to necessary changes only.
10. Physical Security.
GPTW enforces defined security perimeters to protect Company’s sensitive or critical information and information processing facilities. As part of this enforcement, GPTW has restricted access to its sites and buildings to authorized personnel only and implemented physical barriers where applicable, to prevent unauthorized physical access and environmental contamination. GPTW has also separated our information processing facilities we manage physically from those managed by external parties and implemented physical access controls to protect secured areas to ensure that only authorized personnel are allowed access. Access to areas where confidential information is processed or stored is restricted to authorized individuals only. The use of photography, video, audio and other recording equipment, such as cameras in mobile devices in secure areas is restricted. GPTW has developed and implemented a clear desk and clear screen policy.
11. Supplier Relationships.
GPTW has a documented policy for supplier relationships and maintains a list of all suppliers we use.
12. Asset Management.
GPTW has a documented Asset Management Procedure and maintains an asset inventory which is accurate, up to date and aligned with other inventories. In addition, GPTW has a documented Acceptable Use Policy. GPTW’s termination process includes the return of all previously issued physical and electronic assets owned by GPTW.
GPTW has a secure process for Disposal of Media and sensitive information.
13. Compliance.
GPTW maintains a list of applicable legislative, statutory, regulatory and contractual requirements required by the organization. GPTW has an annual independent review of information security and regular technical compliance reviews.
April 16, 2021